Experiencing lags on your computer? You're probably running a miner that consumes 100% of your CPU. Coin Hive (a JavaScript based miner) is becoming rapidly popular among Malware developers.
Coinhive, as a tool, is a JavaScript library that website owners can load on their site. When users access the site, the Coinhive JavaScript code library executes and mines for Monero, but using the user's CPU resources.
Very smart idea as it was meat to be a replacer for publicities. Coinhive launched on September 14, and its authors advertise it as an alternative to classic advertising. Coinhive claims that webmasters can remove ads from their sites, and load the Coinhive library and mine for Monero using a small portion of the user's CPU while the user is navigating the site. Site owners can make money and support their business, but without peppering their visitors with annoying ads.
The idea got some traction, and two days after it launched The Pirate Bay ran it as a test, but dropped it after negative user feedback.
In the few days that have passed after it launched, Coinhive has spread to almost all corners of the malware community.
First, we saw it embedded inside a popular Chrome extension named SafeBrowse, where the Coinhive code was added to run in Chrome's background and mine Monero at all times the browser was running.
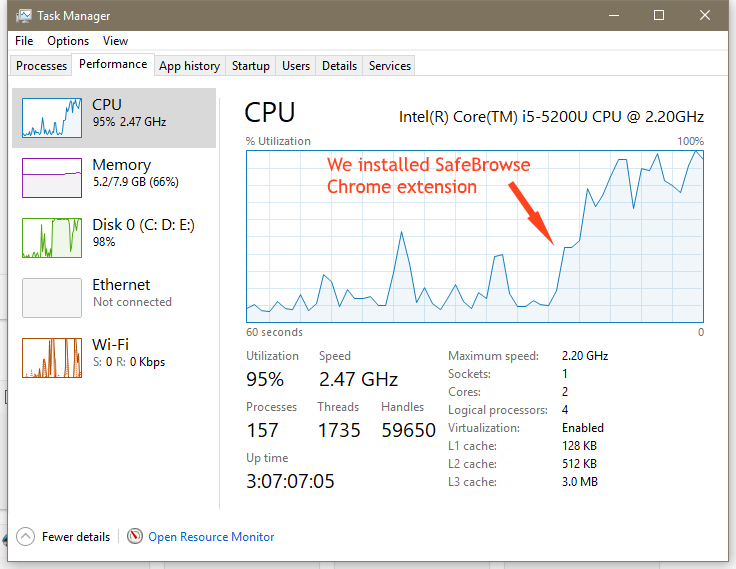
Then, we saw Coinhive embedded in typosquatted domains. Someone registered the twitter.com.com domain name and was loading the Coinhive JS library on the page. Users who mistyped the Twitter URL and ended up on the page would mine Monero for the site's owner.
This would happen for only a few seconds until the user realized he was on the bad page, but that would be enough for the site's owner to generate a profit. In time and with more of these domains in hand, the owner of all those mistyped site URLs would make a nice profit.
After that, security researchers discovered hacked sites where intruders modified the site's source code and secretly loaded the Coinhive miner.
The miner used a configuration to mine Monero for the hacker's personal account, but using the CPU power of unsuspecting users who accessed the hacked sites. Researchers found hacked WordPress and Magento sites modified this way.
In addition, security experts also found one of the biggest malvertising groups deploying the Coinhive script.
Malicious ads would redirect users to tech support scams, where besides the classic fake virus alerts, crooks would also load Coinhive in the browser and mine for Monero while victims were trying to figure out if the site was valid or not.
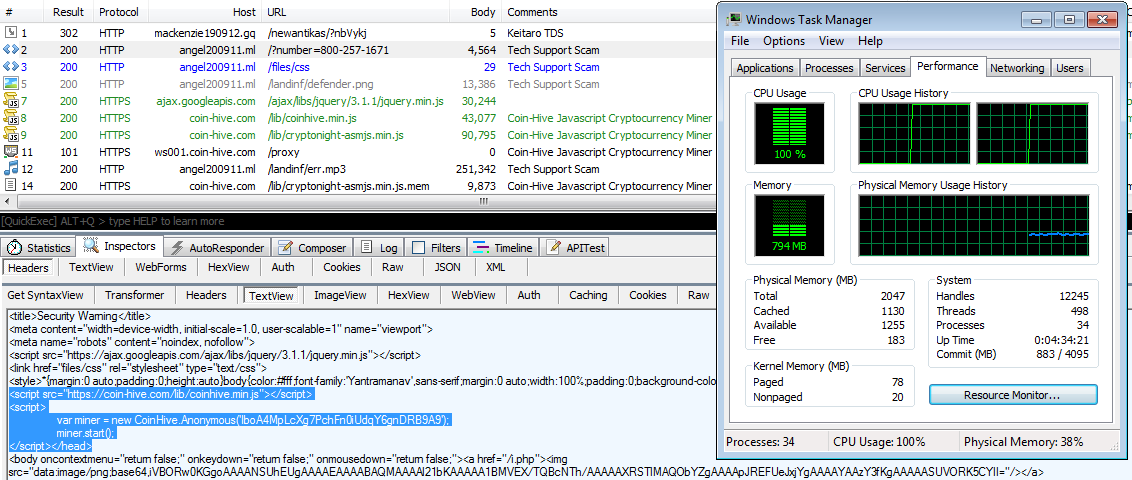
The most recent case of Coinhive being deployed alongside malware came to light earlier today when a researcher found a site peddling a fake Java update that was also mining for Monero using Coinhive.
It is crystal clear that malware authors found their next payday in Coinhive. The next place Bleeping Computer expects to see Coinhive deployed next is adware, and especially the type of adware that hijacks search fields and inserts ads into search results.
Adware is already pretty noisy as it is by making visible changes to the user's browser. There's nothing stopping adware devs from loading the Coinhive library in the background and mining a few extra Monero before the user notices either the intrusive ads, the change in browser homepage, or the noticeable CPU drag.
While the Coinhive team has made it pretty clear that responsibility for how the library is used falls entirely on the person deploying the miner, malware devs are notoriously unreliable when it comes to abiding rules and regulations.
The websites of US telly giant CBS's Showtime contained JavaScript that secretly commandeered viewers' web browsers over the weekend to mine cryptocurrency.
The flagship Showtime.com and its instant-access ShowtimeAnytime.com sibling silently pulled in code that caused browsers to blow spare processor time calculating new Monero coins – a privacy-focused alternative to the ever-popular Bitcoin. The hidden software typically consumed as much as 60 per cent of CPU capacity on computers visiting the sites.
The normal use of this Miner on legit web sites without a lot of traffic seems to be generating a little revenue which wouldn't seem as an option to replace existing ads.
Some have also predicted the Coinhive cryptojacking disaster. For example, at least two ad blockers have added support for blocking Coinhive's JS library — AdBlock Plus and AdGuard.
In addition, developers have also put together Chrome extensions that scan your browser and terminate anything that looks like Coinhive's miner script — AntiMiner, No Coin, and minerBlock.
While this year might be remembered for the WannaCry and NotPetya ransomware outbreaks and the CCleaner and Equifax breaches, silently, cryptocurrency miners have been one of the most active and prevalent threats.
This past two weeks, Kaspersky reported seeing over 1.65 million computers infected with cryptocurrency mining malware in the first eight months of the year, and IBM also reported a spike in cryptocurrency malware installed on enterprise networks.
Currently, according to the Coinhive team, the library's launch appeared to have exceeded expectations. Even if developed with good intentions, Coinhive's name and reputation is bound to be smeared in the dirt if malware authors continue the trend they're currently on.
Source: https://www.bleepingcomputer.com/news/security/coinhive-is-rapidly-becoming-a-favorite-tool-among-malware-devs/
Coinhive, as a tool, is a JavaScript library that website owners can load on their site. When users access the site, the Coinhive JavaScript code library executes and mines for Monero, but using the user's CPU resources.
Very smart idea as it was meat to be a replacer for publicities. Coinhive launched on September 14, and its authors advertise it as an alternative to classic advertising. Coinhive claims that webmasters can remove ads from their sites, and load the Coinhive library and mine for Monero using a small portion of the user's CPU while the user is navigating the site. Site owners can make money and support their business, but without peppering their visitors with annoying ads.
The idea got some traction, and two days after it launched The Pirate Bay ran it as a test, but dropped it after negative user feedback.
Malware operations adopt Coinhive
Unfortunately, despite the clever use of a Monero miner, Coinhive is in the situation of other useful tools that have been abused by crooks.In the few days that have passed after it launched, Coinhive has spread to almost all corners of the malware community.
First, we saw it embedded inside a popular Chrome extension named SafeBrowse, where the Coinhive code was added to run in Chrome's background and mine Monero at all times the browser was running.

Then, we saw Coinhive embedded in typosquatted domains. Someone registered the twitter.com.com domain name and was loading the Coinhive JS library on the page. Users who mistyped the Twitter URL and ended up on the page would mine Monero for the site's owner.
This would happen for only a few seconds until the user realized he was on the bad page, but that would be enough for the site's owner to generate a profit. In time and with more of these domains in hand, the owner of all those mistyped site URLs would make a nice profit.
After that, security researchers discovered hacked sites where intruders modified the site's source code and secretly loaded the Coinhive miner.
The miner used a configuration to mine Monero for the hacker's personal account, but using the CPU power of unsuspecting users who accessed the hacked sites. Researchers found hacked WordPress and Magento sites modified this way.
In addition, security experts also found one of the biggest malvertising groups deploying the Coinhive script.
Malicious ads would redirect users to tech support scams, where besides the classic fake virus alerts, crooks would also load Coinhive in the browser and mine for Monero while victims were trying to figure out if the site was valid or not.

The most recent case of Coinhive being deployed alongside malware came to light earlier today when a researcher found a site peddling a fake Java update that was also mining for Monero using Coinhive.
It is crystal clear that malware authors found their next payday in Coinhive. The next place Bleeping Computer expects to see Coinhive deployed next is adware, and especially the type of adware that hijacks search fields and inserts ads into search results.
Adware is already pretty noisy as it is by making visible changes to the user's browser. There's nothing stopping adware devs from loading the Coinhive library in the background and mining a few extra Monero before the user notices either the intrusive ads, the change in browser homepage, or the noticeable CPU drag.
While the Coinhive team has made it pretty clear that responsibility for how the library is used falls entirely on the person deploying the miner, malware devs are notoriously unreliable when it comes to abiding rules and regulations.
The websites of US telly giant CBS's Showtime contained JavaScript that secretly commandeered viewers' web browsers over the weekend to mine cryptocurrency.
The flagship Showtime.com and its instant-access ShowtimeAnytime.com sibling silently pulled in code that caused browsers to blow spare processor time calculating new Monero coins – a privacy-focused alternative to the ever-popular Bitcoin. The hidden software typically consumed as much as 60 per cent of CPU capacity on computers visiting the sites.
The normal use of this Miner on legit web sites without a lot of traffic seems to be generating a little revenue which wouldn't seem as an option to replace existing ads.
 |
| First week results from COIN-HIVE |
Community reacts to prevent cryptojacking
Currently, some experts refer to the technique of hijacking users' browsers for cryptocurrency mining as "cryptojacking."Some have also predicted the Coinhive cryptojacking disaster. For example, at least two ad blockers have added support for blocking Coinhive's JS library — AdBlock Plus and AdGuard.
In addition, developers have also put together Chrome extensions that scan your browser and terminate anything that looks like Coinhive's miner script — AntiMiner, No Coin, and minerBlock.
While this year might be remembered for the WannaCry and NotPetya ransomware outbreaks and the CCleaner and Equifax breaches, silently, cryptocurrency miners have been one of the most active and prevalent threats.
This past two weeks, Kaspersky reported seeing over 1.65 million computers infected with cryptocurrency mining malware in the first eight months of the year, and IBM also reported a spike in cryptocurrency malware installed on enterprise networks.
Currently, according to the Coinhive team, the library's launch appeared to have exceeded expectations. Even if developed with good intentions, Coinhive's name and reputation is bound to be smeared in the dirt if malware authors continue the trend they're currently on.
Source: https://www.bleepingcomputer.com/news/security/coinhive-is-rapidly-becoming-a-favorite-tool-among-malware-devs/

Only wanna tell that this is very useful , Thanks for taking your time to write this.
ReplyDeleteclipping path service
Photo Retouching service
Raster To vector conversion
The Persistence of your work Gives a lots of Knowledge...Insightful Contents are Shared about Javascript Training...Thanks!!!
ReplyDeleteJava training in chennai | Java training in annanagar | Java training in omr | Java training in porur | Java training in tambaram | Java training in velachery