The U.S. Justice Department announced charges on Wednesday against three dozen individuals thought to be key members of ‘Infraud,” a long-running cybercrime forum that federal prosecutors say cost consumers more than a half billion dollars. In conjunction with the forum takedown, 13 alleged Infraud members from the United States and six other countries were arrested.
Started in October 2010, Infraud was short for “In Fraud We Trust,” and collectively the forum referred to itself as the “Ministry of Fraudulently [sic] Affairs.” As a mostly English-language fraud forum, Infraud attracted nearly 11,000 members from around the globe who sold, traded and bought everything from stolen identities and credit card accounts to ATM skimmers, botnet hosting and malicious software.

“Today’s indictment and arrests mark one of the largest cyberfraud enterprise prosecutions ever undertaken by the Department of Justice,” said John P. Cronan, acting assistant attorney general of the Justice Department’s criminal division. “As alleged in the indictment, Infraud operated like a business to facilitate cyberfraud on a global scale.”
The complaint released by the DOJ lists 36 Infraud members — some only by their hacker nicknames, others by their alleged real names and handles, and still others just as “John Does.” Having been a fairly regular lurker on Infraud over the past seven years who has sought to independently identify many of these individuals, I can say that some of these names and nick associations sound accurate but several do not.
The government says the founder and top member of Infraud was Svyatoslav Bondarenko, a hacker from Ukraine who used the nicknames “Rector” and “Helkern.” The first nickname is well supported by copies of the forum obtained by this author several years back; indeed, Rector’s profile listed him an administrator, and Rector can be seen on countless Infraud discussion threads vouching for sellers who had paid the monthly fee to advertise their services in “sticky” threads on the forum.
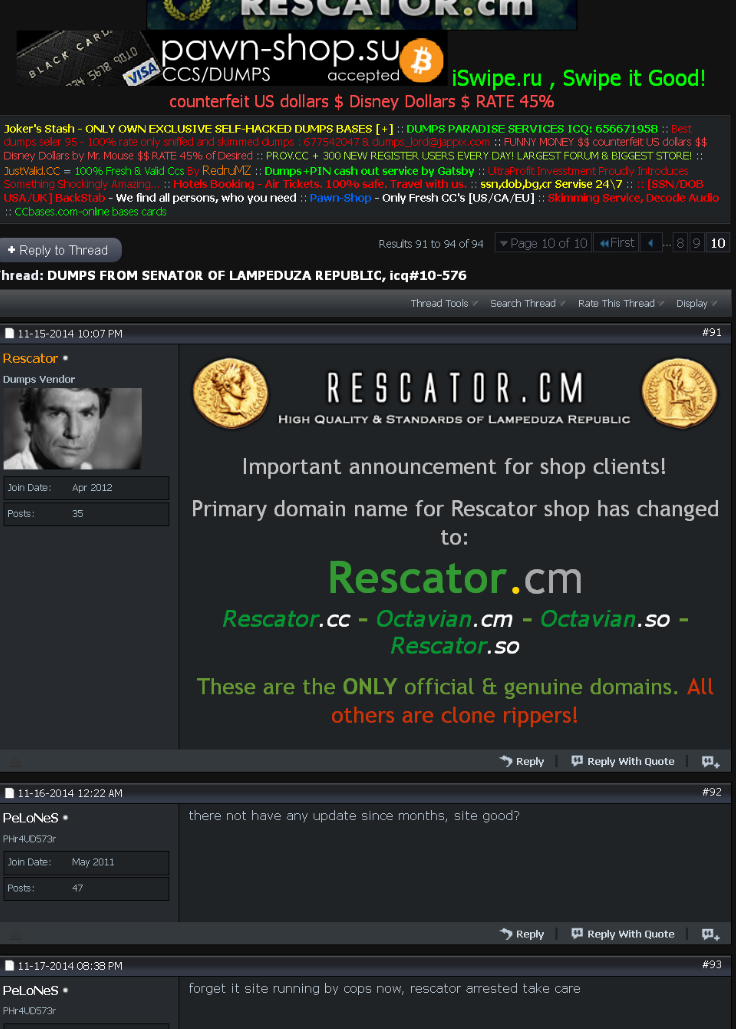
Also, Rescator was a separate vendor on Infraud, and there are no indications that I could find suggesting that Rector and Rescator were the same people. Here is Rescator’s most recent sales thread for his credit card shop on Infraud — dated almost a year after the Target breach. Notice the last comment on that thread alleges that Rescator had recently been arrested and that his shop was being run by law enforcement officials:
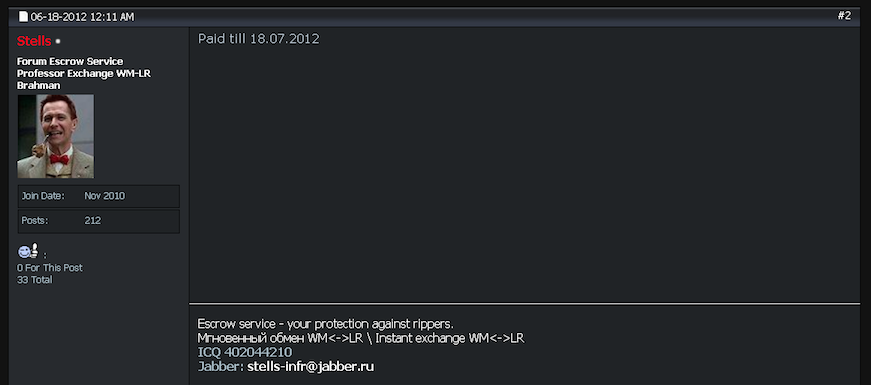
Another top administrator of Infraud used the nickname “Stells.” According to the Justice Department, Stells’ real name is Sergey Medvedev. The government doesn’t describe his exact role, but it appears to have been administering the forum’s escrow service.
Most large cybercrime forums have an escrow service, which holds the buyer’s virtual currency until forum administrators can confirm the seller has consummated the transaction acceptably to both parties. The escrow feature is designed to cut down on members ripping one another off — but it also can add considerably to the final price of the item(s) for sale.
In April 2016, Medvedev would take over as the “admin and owner” of Infraud, after he posted a note online saying that Bondarenko had gone missing, the Justice Department said.
One defendant in the case, a well-known vendor of stolen credit and debit cards who goes by the nickname “Zo0mer,” is listed as a John Doe. But according to a New York Times story from 2006, Zo0mer’s real name is Sergey Kozerev, and he hails from St. Petersburg, Russia.
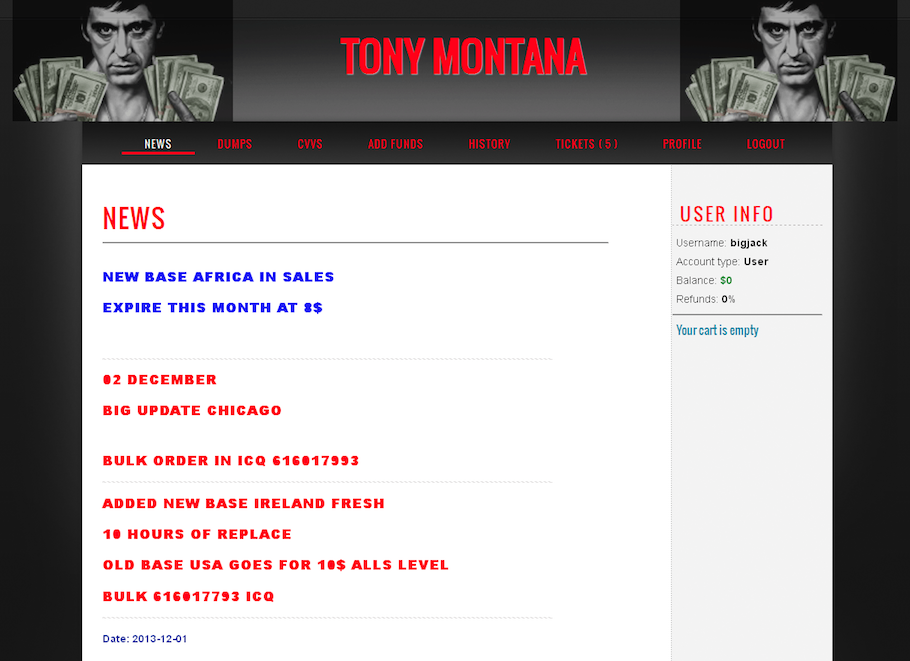
The indictments also list two other major vendors of stolen credit and debit cards: hackers who went by the nicknames “Unicc” and “TonyMontana” (the latter being a reference to the fictional gangster character played by Al Pacino in the 1983 movie Scarface). Both hackers have long operated and operate to this day their own carding shops:
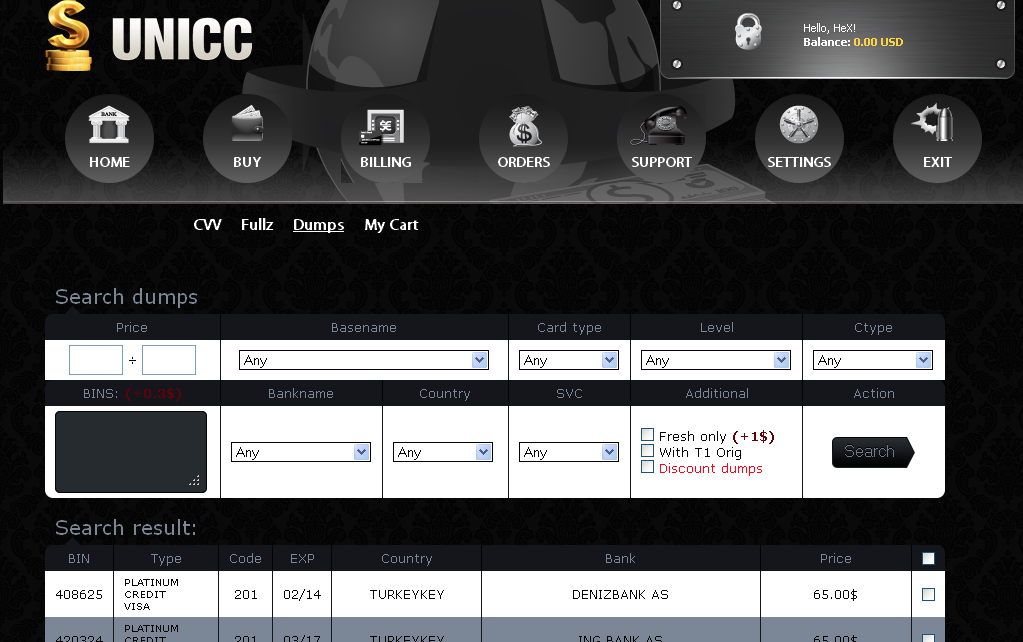
Unicc
shop, which sells stolen credit card data as well as Social Security
numbers and other consumer information that can be used for identity
theft.
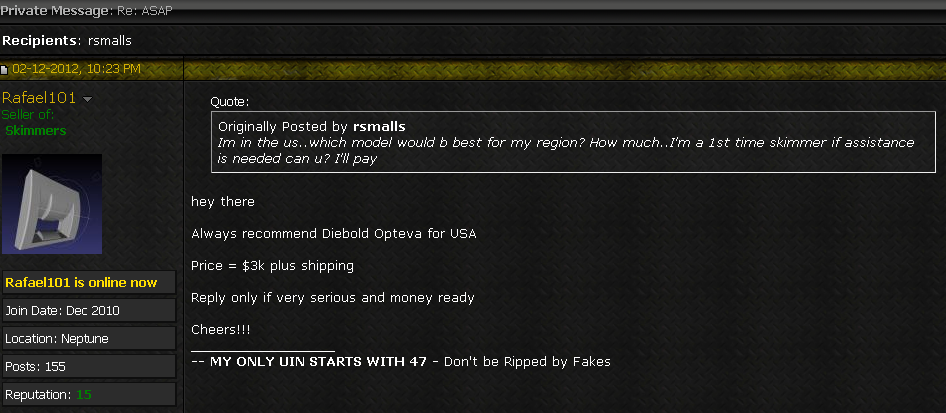
Perhaps the most successful vendor of skimming devices made to be affixed to ATMs and fuel pumps was a hacker known on Infraud and other crime forums as “Rafael101.” Several of my early stories about new skimming innovations came from discussions with Rafael in which this author posed as an interested buyer and asked for videos, pictures and technical descriptions of his skimming devices.
A confidential source who asked not to be named told me a few years back that Rafael had used the same password for his skimming sales accounts on multiple competing cybercrime forums. When one of those forums got hacked, it enabled this source to read Rafael’s emails (Rafael evidently used the same password for his email account as well).
The source said the emails showed Rafael was ordering the parts for his skimmers in bulk from Chinese e-commerce giant Alibaba, and that he charged a significant markup on the final product. The source said Rafael had the packages all shipped to a Jose Gamboa in Norwalk, Calif — a suburb of Los Angeles. Sure enough, the indictment unsealed this week says Rafael’s real name is Jose Gamboa and that he is from Los Angeles.
The Justice Department says the arrests in this case took place in Australia, France, Italy, Kosovo, Serbia, the United Kingdom and the United States. The defendants face a variety of criminal charges, including identity theft, bank fraud, wire fraud and money laundering. A copy of the indictment is available here.

Hello all
ReplyDeleteam looking few years that some guys comes into the market
they called themselves hacker, carder or spammer they rip the
peoples with different ways and it’s a badly impact to real hacker
now situation is that peoples doesn’t believe that real hackers and carder scammer exists.
Anyone want to make deal with me any type am available but first
I‘ll show the proof that am real then make a deal like
Available Services
..Wire Bank Transfer all over the world
..Western Union Transfer all over the world
..Credit Cards (USA, UK, AUS, CAN, NZ)
..School Grade upgrade / remove Records
..Spamming Tool
..keyloggers / rats
..Social Media recovery
.. Teaching Hacking / spamming / carding (1/2 hours course)
discount for re-seller
Contact: 24/7
fixitrogers@gmail.com
Wow, So amazing information share this post. Actually i have clipping path service website and this post are so help me improve for my work. I appreciate you sharing this blog article.
ReplyDelete